Outline of R&D
Realization of a Society that can Use Cybernetic Avatars Safely and Securely
1. Position in the program
With the aim to ‘be free from limitations of body, brain, space, and time’, this project will examine the results of Socio-CA’s and In-Body CA’s across the board, identify technical and institutional issues common to these different CA’s. Moreover, to provide a forum for collecting opinions from its citizens and make proposals for solving the issues in Japan and abroad. The goal is to build a CA infrastructure which ensures ‘safety, security, and trust’ and enhances social acceptability.
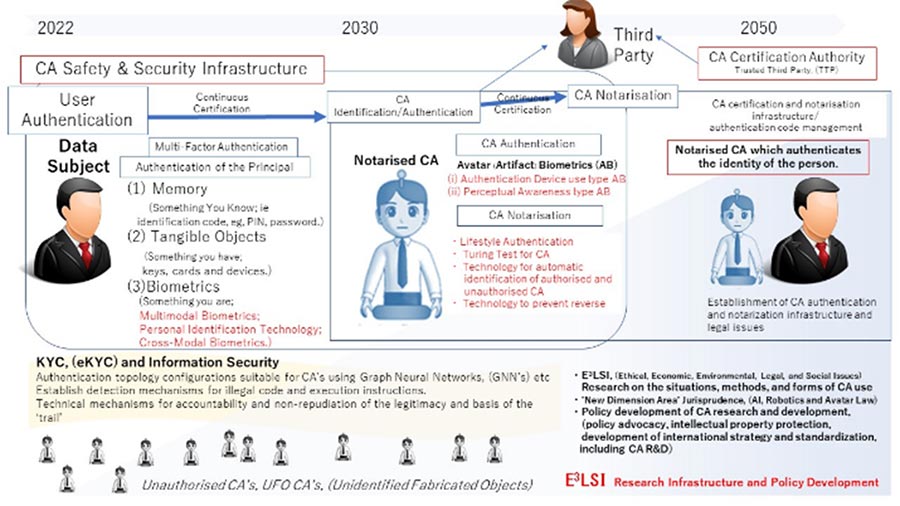
In particular, the project will contribute to the realizing of Target1, ‘CA infrastructure’ by building a ‘safety and security assurance infrastructure’ to ensure the safety and security of CA use by addressing such issues as operator impersonation, CA hijacking, and illegal acquisition of technical information, etc, stored within CA’s, (illegal imitation of skills). (Fig. 1)
At the same time, this project will promote research on ‘ethical, economic, environmental, legal, and social issues, (E3LSI)’ in order to realize Target 2, ‘Proposing a new way of life based on socially accepted ideas’.

2. Overview of the R&D and the Challenges
The project aims to realise a CA safety and security assurance infrastructure which will ensure safety/security /reliability and increase the social acceptability of CA’s, thereby opening up a new communication civilisation via them. We will promote research and development projects by dividing them into the following three specific research and development items: (Fig. 2)
(i) inter-project collaboration/demonstration management
Co-ordination with the Demonstration Experiments and Reliability Assurance Infrastructure of each project under Moonshot Objective 1, co-ordination summary of E3LSI issues, retrieval system for technical/results information, and data management.
(ii) construction of CA safety and security assurance infrastructure
Through the development of these technologies, the aim will be to build such safe and secure CA operation.
CA operator authentication, (user authentication technology)
Technology to check who the operator is by making full use of various authentication technologies at the same time.
Identification/authentication of CA’s, (CA Authentication)
The CA will be used to check that it has not been hijacked by someone else or impersonated.
Assurance of the linkage between, and existence of the operator and the CA, (CA Notarisation)
Technology to prove the identity of the operator by an authorised CA.
(iii) Research on E3LSI issues and policy development
Build an organisation to conduct E3LSI research regarding CA’s, in co-operation with legal research about new related dimensions such as AI/Robotics/Avatar Law, intellectual property strategy, international macro-economics and econometrics research. We will establish a base for research, study and policy-making about the social acceptability of CA’s through a cycle of policy recommendations and the consolidation of opinions from various perspectives. Through these activities, we aim to build a social infrastructure which enables the safe and secure use of CA’s.
3. Future plans
Proposition of applicable user authentication, CA certification/notarisation technologies for Socio-/In-Body CA’s developed by each project under Goal 1, and conduct research to establish a safety/security assurance infrastructure which can ensure them by combining these technologies. Creation of an organisation to disseminate laws and policies necessary to promote a CA lifestyle. We aim to develop a research system capable of comprehensively and sustainably studying the E3LSI issues. which need to be considered in order to develop the related, necessary institutional systems for the above purposes.